Good news! NSFW is now a thing of the past. Phew!
Nothing is unsafe for work anymore as long as you work in the privacy of your own home. Call it a moratorium on office etiquette. The new, relaxed work ethic means no more management snooping, no judging by colleagues and no more having to position your monitor to avoid surprises. At least as long as you can keep the kids out of your home office.
But the future of tech-fueled teleworking may not be as rosy as it looks. Yes, you can now click on every hilarious meme and compulsively view dozens of videos before getting reacquainted with the inexorable passage of time as dinner time approaches. But behind some of that dopamine-secreting, productivity-devouring clickbait lies a potential panoply of threats self-isolating workers should be familiar with, at least in passing. I know this is pushing it, but I’m going to briefly cover four examples

1.Cyber extortion
2.Cyberfraud
3.Clickbait
4.Surveillance
Can you handle it?
(To help alleviate the effects of modern attention spans, I am interspersing the next few paragraphs with cute images of adorable kittens. You’re welcome.)
All strapped in? Here we go.
1. Cyber extortion aims to intimidate, embarrass and humiliate
In a handful of reported cases, grown men lured by the promise of ‘making new friends’ online and subsequently sharing intimate images in the hope of reciprocity were shocked — shocked! — only to discover that they were the victims of bait and switch techniques designed to separate them from their money, under threat of public and embarrassment. While we never hear from the ones who comply, those who did not painted a terrifying picture of an underworld of sex workers used to lure and seduce for profit.

A variation on this sextortion technique has already been reported thousands of times this year. It begins ominously enough with the email subject “I’ve got nude pictures of you” or simply prints the victim’s password in the subject line. It then proceeds to claim that IoT cameras around the house have been hijacked to take surreptitious images of of the victim.
Claudiu Popa: the new NSFW is cyberfraud, clickbait, malware, surveillance, and the risk of data privacy breaches. That’s all.
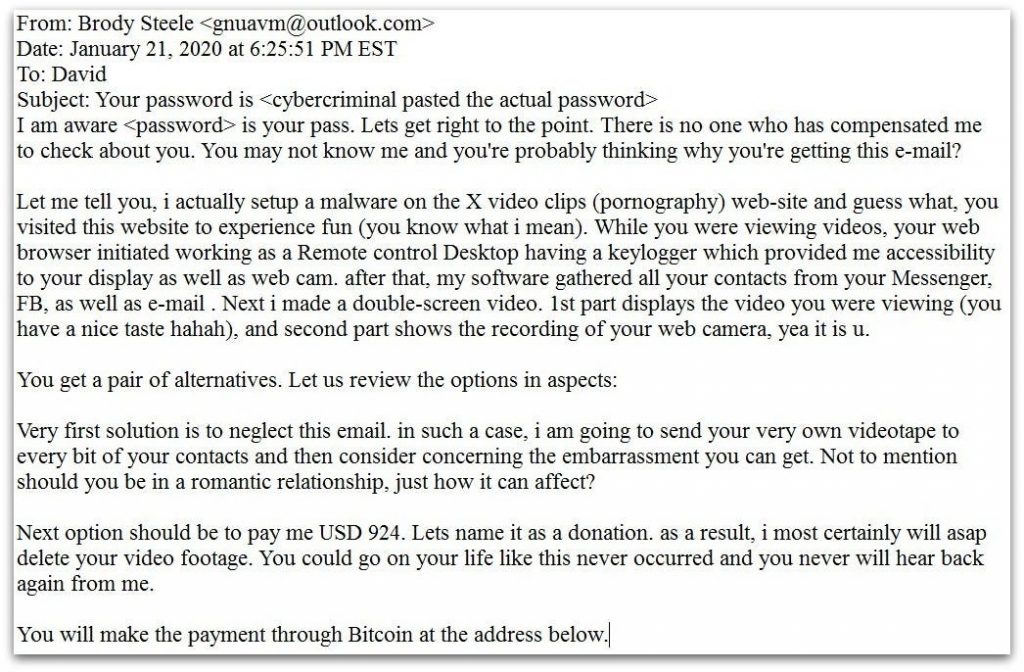
This is a bluff, but a fairly convincing one because the password is real: usually an old one from an ancient database making the rounds on the internet. Some people may not be aware of their email address and other identity elements being peddled online as a result of some scale data breach or another. If you’re working from home, you need to be aware of the need to ensure your passwords are unique to sites and accounts, never to be reused. This is a tactic used to prevent password stuffing attacks, where a single password provides criminals with the opportunity to ‘stuff’ the Internet’s top sites with the one password they managed to get their hands on, in the hopes of stumbling of another site that uses the same username/password combo. According to a recent Google report, an estimated 65 percent of people use just one password for multiple or all of their accounts.
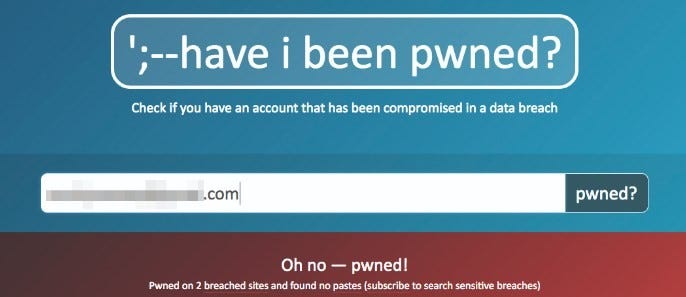
Curious about what data breaches your email might have been exposed in? Check out Have I Been Pwned and do yourself a favour: set up an alert to ensure the site notifies you next time it happens. It’s important to remember that the best course of action is to ignore these types of spammy scams but to still change your password, just in case. If multifactor authentication is available, use it. If not, at least set yourself up with a long passphrase instead of a weak password, and store it safely in a password database trusted by experts.

2. Cyberfraud uses deception to separate victims from their money
The Canadian Anti Fraud Centre released an Alert Bulletin this month warning about the rise in the numbers and diversity of scams targeting teleworkers. By some estimates that number of people has risen to 1 billion globally this month. That undoubtedly represents an irresistible target for cybercriminals who desperately try to get email recipients to open infected email attachments, by fear, curiosity or simply to validate the suspicion that the email is a scam. It’s a phishing game, and the only way to win is to ignore these messages.

In the above message, the attached invoice was simply a ruse to get people to open the Office document, deactivate macro protection and watch as malware makes itself at home on the computer, probably stealing and encrypting files before demanding a hefty ransom. The example is one of late payment, but the message could have just as impersonated the Public Health Agency of Canada to communicate alarming announcements indicating that results are in and the recipient is infected with COVID 19. Or the CDC, WHO, Red Cross, Revenue Canada, etc.

3. Clickbait uses misdirection, suggestion and psychology to hide malware
Unlike phishing email, most clickbait lives online and the tempting lure of promised deals and seductive offers can be enough to click on a pop-up, a social media contest (better participate, just in case), or a pesky message that clearly looks like a mistake but people just need to click to get it off their screen.

Unfortunately the malware that installs itself once the clicking happens is anything but benign. In many cases, it will also be a program that scours your computer looking for data to steal first, then encrypt to make it unusable. Any connected backups will also be encrypted before popping up a message indicating that it is awaiting payment in exchange for your data back.
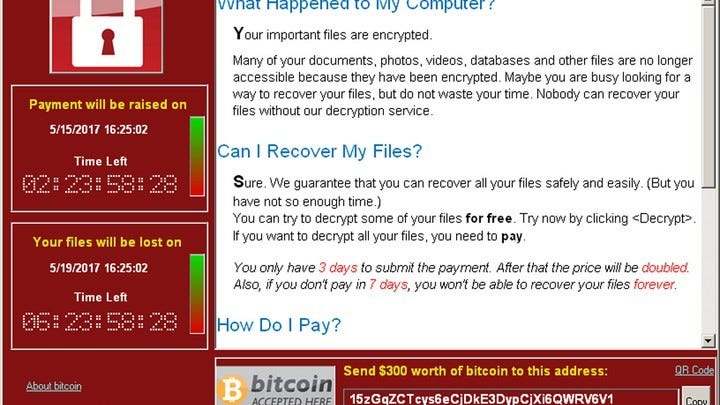
Other types of insidious malware include keyloggers, programs that once installed, surreptitiously monitor your keyboard, mouse and screen to filter anything that looks like account credentials and specifically passwords. It watches, silently, day after day, until it the data is finally sent to its home servers and in to the hands of criminals.
Hang in there, you can do this! Here are more cats to keep you going through this final stretch!

4. Data aggregation as a form of surveillance
The following is not illegal, but some organizations are taking the opportunity afforded by the explosion in numbers of teleworkers to spread their wares and collect copious amounts of data about them. While most people would be surprised to discover that teleworking tools like Zoom and Join.me or any of the myriad videoconferencing options do overcollect information, the fact is that most of these companies are at least a little transparent about their practices…as long as everyone takes the time to read privacy policies and terms of service before kissing their privacy expectations goodbye.

If you are already using this technology, the company simply assumes you’re okay with sharing behavioural data, notifying call organizers when you have switched away from the conversation window, your name, physical address, email address, phone number, job title, employer, what type of device you are using, and your IP address and any “information you upload, provide, or create while using the service.”
As for whether Zoom sells user data, a quick parsing of the company’s Privacy Policy should be sufficient to convince the reader that the answer is … nuanced.

As always, privacy is largely a matter of consent and we should all be a bit more thrifty when handing it out for the sake of convenience. What is safe for work today is no longer about what we can get away with (or whether we can hit the ‘boss key’ in time), but about the risks we take with company devices, data, productivity and ultimately control over our most personal asset: our identity.


Member discussion: